Phishing is a social engineering tactic that sees hackers attempt to gain access to personal or confidential information by posing as a legitimate company. In this article, Cyber Security Hub’s editor Olivia Powell explores what phishing attacks are, why malicious actors launch phishing attacks and how companies can protect themselves against them.
For our guide explaining the different types of malware and how this can affect your business, visit Cyber Security Hub’s Ultimate guide to malware.
Contents
- Why do hackers launch phishing attacks?
- Phishing attacks that target individuals
- Phishing attacks that target companies
- Phishing attacks and cryptocurrency
- How to protect against phishing attacks
Why do hackers launch phishing attacks?
Phishing attacks soared in 2022, with international consortium and fraud prevention group the Anti-Phishing Working Group recording a total of 3,394,662 phishing attacks in the first three quarters of 2022. There were 1,025,968 attacks in Q1, growing to 1,270,883 attacks in the third quarter, with each quarter breaking the record as the worst quarter APWG has ever observed.
Ernie Moran, general manager of automated prepaid card fraud protection software Arden at financial protection service Brightwell, believes that 2023 will continue to see a rise in phishing attacks due to more people turning to cyber crime for financial gain.
“The downturn in the economy this year will almost certainly lead to an increase in individuals taking additional risks to commit fraud in 2023, but many financial organizations are still unprepared to identify and take action on a coordinated and targeted fraud attack,” he explains.
“The downturn in the economy this year will almost certainly lead to an increase in individuals taking additional risks to commit fraud” – Ernie Moran, general manager of Arden at Brightwell
This financial gain may be from harvesting personal or banking information from individuals and either using or selling it. It may also be gained via accessing confidential information held by companies. They may do this with the goal of extorting the company, or to sell the stolen information to other bad actors on the dark web.
Malicious actors can use a variety of channels to send phishing attempts including texts, social media messages and emails. They can also use a variety of phishing techniques in order to gain access to this information.
Phishing attacks that target individuals
Malicious actors that use phishing attacks against individuals pose as legitimate companies. This is because victims are more likely to click on a link from a source they believe is trustworthy. These attacks are often used to harvest login credentials, personal data or payment information from victims, which can either be sold to other bad actors on the dark web or used to commit credit card fraud or identity theft.
These phishing scams are supposed to appear legitimate, so they often use channels typically deployed by companies to communicate with their customers, like email. As an example, I recently received an email from hackers attempting to phish me by posing as Apple.
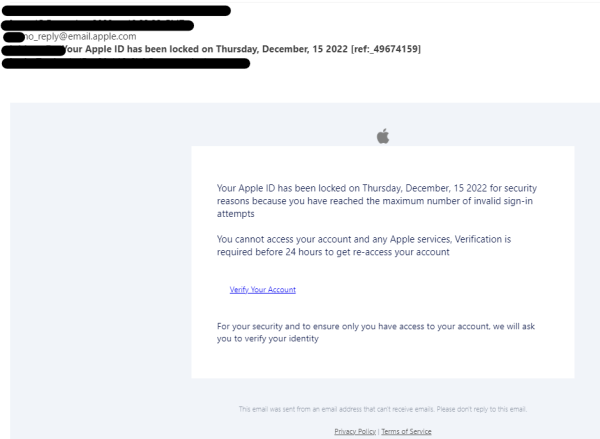
The use of a spoofed ‘no reply’ email address and a reference number also serve to make it look more legitimate.
Malicious actors may also use text-based phishing, known as SMSishing or smishing, to pose as a genuine company.
Starting in November 2020 in the UK, a number of people reported being targeted by phishing attacks where malicious actors posed as the Royal Mail service, claiming that they needed to pay a fee for a parcel to be delivered. As potential victims are used to receiving updates from delivery services including Royal Mail via text message, this makes the message seem more legitimate.
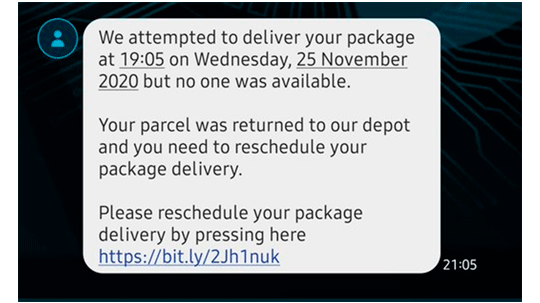
Image source: the Royal Mail website
If someone entered their card details onto the site, their payment details were harvested. These details may have been sold on dark web sites dedicated to the trading and unauthorized use of credit card details, known as carding sites.
With 134 in every 1000 people in the UK becoming a victim of credit card fraud per year, with an annual cost of £8,833.20 (US$10,626.30) per 1000 people, phishing attacks like these are doing significant damage.
Phishing attacks that target companies
Companies and their employees can also be targeted by phishing attacks. These attacks are referred to as spear phishing attacks.
These types of attacks are increasingly common, with the majority (65 percent) of cyber attackers using spear phishing as their primary attack vector, according to cyber security company Phishing Box.
Their aim is to either harvest data belonging to the businesses’ customers, or to access data belonging to the business itself.
Phishing attacks to harvest customer data
Malicious actors may use spear phishing attacks to harvest large amounts of customer data held by said companies. They may do this to extort companies using the threat of a data leak, to sell the information over the dark web or to data brokers, or to use the data for other nefarious purposes including identity theft.
A phishing attack in August 2022 against communications company Twilio led to 163 companies, each with hundreds of customers of their own, being affected by a data breach directly tied to the attack.
The breach, dubbed Oktapus by researchers, involved a targeted phishing attack against Twilio employees to gain unauthorized access to the company’s servers and its customer data.
The communications platform disclosed that it identified 163 Twilio customers whose “data was accessed without authorization for a limited period of time”. In addition, 93 users of the two-factor authentication app Authy, which Twilio owns, saw their accounts accessed and additional devices registered by bad actors. Following the breach, Twilio notified all users that had their accounts accessed and has removed all unauthorized devices.
The Twilio data breach CS Hub reported on recently has developed further, with the communications company reporting that 163 companies that use its service have been affected by the breach.
Discover more: https://t.co/JB206EC0qu#cybersecurity #databreach #phishing #Twilio— Olivia Powell (@CSHubEditor) September 1, 2022
After the attack took place, a number of companies reported that their customer data was compromised during the breach, including messaging app Signal, who reported 1,900 users may have had their phone numbers revealed to hackers, with some users directly targeted.
Food delivery company DoorDash said that a “small percentage of individuals whose data is maintained by DoorDash” had their personal data including name, email address, delivery address and phone number. In addition, a smaller number of customers had their “basic order information and partial payment card information” accessed during this data breach.
In response to the attack, Twilio enforced “a number of additional measures internally to protect against these attacks”, including “hardening security controls at multiple layers”.
Phishing attacks to harvest company data
Malicious actors may also use spear phishing attacks to harvest data relating to the company itself, for example information used to access the company’s network, source code information or other proprietary data.
In October 2022, cloud storage company Dropbox had its source code stolen by hackers after its employees were targeted by a phishing attack.
The attack saw a malicious actor pose as code integration and delivery platform CircleCI in order to harvest login credentials and authentication codes from employees. It was also able to access Dropbox’s account on code repository site GitHub, as CircleCI login information can be used to log in to the site.
Through the attack, the hacker gained access to some of the code Dropbox stores on the platform, including API keys used by its developers.
Dropbox was alerted to the breach by GitHub after suspicious activity was noticed on its account. The hacker was able to access and copy the code for 130 of Dropbox’s code repositories, although this did not contain any code for its core apps or infrastructure.

Image source: Yancy Min on Unsplash
Dropbox assured users that the threat actor did not gain access to the contents of any Dropbox accounts, passwords or payment information. Instead, the hacker was able to access a “few thousand names and email addresses belonging to Dropbox employees, current and past customers, sales leads and vendors”. The company said the risk to those who had their information accessed in the breach was “minimal”, but all those affected were contacted.
GitHub itself reported a similar phishing attack in September 2022, involving a malicious actor posing as CircleCI to gain access to various user accounts.
The phishing site used by the hacker relayed time-based-one-time-passwords (TOTP) used for two-factor-authentication codes to the hacker in real time, allowing them to gain access to accounts protected by TOTP two-factor authentication. Accounts protected by hardware security keys were not vulnerable to this attack.
Through the attack, the malicious actor was able to gain access to and download multiple private code repositories. This enabled it to use techniques to preserve its access to the account even in the event that the compromised user or organization changed their password.
Phishing attacks and cryptocurrency
Bad actors launching phishing attacks primarily do so for financial gain, whether this is through the theft of payment or banking information, or by selling information gathered through phishing attacks.
With Bitcoin, Ethereum and Tether having market caps of $330.6bn, $152.6bn and $68.2bn respectively, cryptocurrency traders and wallets can be an attractive target for phishing attacks. So much so that Blockchain data platform Chainanalysis reported that a total of $3.8bn in cryptocurrency was stolen in 2022.
Phishing attacks against those who own cryptocurrency can have large payouts. In October 2022, a hacker known as Monkey Drainer used phishing attacks to steal $1mn worth of Ethereum and NFTs in just 24 hours.
1/ Over the past 24 hrs ~700 ETH ($1m) has been stolen by the phishing scammer known as Monkey Drainer.
They recently surpassed 7300 transactions from their drainer wallet after being around for only a few months. pic.twitter.com/6vAYBiqCxQ
— ZachXBT (@zachxbt) October 25, 2022
Monkey Drainer is notorious for using phishing-based hacking techniques to steal from victims by setting up fake cryptocurrency and NFT sites.
To make these fake sites more believable, Monkey Drainer has been known to pose as legitimate blockchain sites including RTFKT and Aptos. After logging in to the fraudulent sites, victims enter sensitive details about their cryptocurrency wallets and sign off on transactions, allowing Monkey Drainer to access their wallets and their funds.
The most prominent victims in the October 2022 attack were referred to only as 0x02a and 0x626. The pair lost a collective $370,000 via malicious phishing sites operated by Monkey Drainer, with 0x02a losing 12 NFTs worth around $150,000.
0x626 held around $2.2mn in their cryptocurrency wallet at the time, however, some of the transactions pushed by Monkey Drainer were rejected by the network the wallet was held on, as they were marked as suspicious. This meant that the overall actual loss was $220,000 worth of cryptocurrency.
Preventing phishing attacks
Teri Radichel, author of Cybersecurity for Executives in the Age of Cloud and CEO of cyber security training and consultancy company 2nd Sight Lab, says that is clear that attacks leveraging phishing and credentials are not going away.
When building their security strategy and threat defense protocols, Radichel suggests that companies “use a layered security approach to prevent damage if and when attackers compromise credentials”, both to defend against and mitigate these attacks. Additionally, Radichel notes that attackers are moving beyond basic web attacks to more sophisticated forms of attacks by leveraging automation and cloud environments.
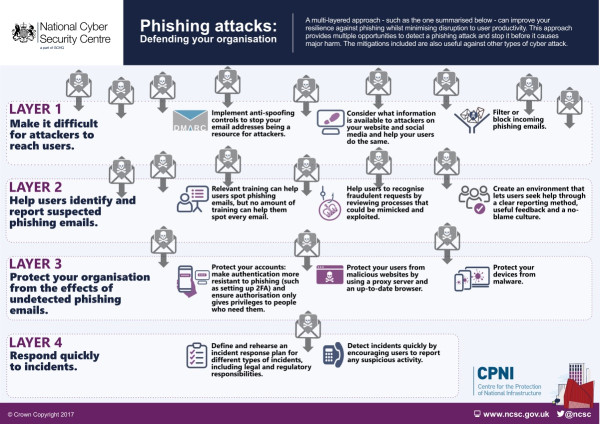
Image source: the UK National Cyber Security Center (NCSC)
When considering phishing attacks that target individuals, the Canadian Center for Cyber Security (CCCS) provides the following advice:
- Verify links before you click them. Hover over the link to see if the info (sender/website address) matches what you expect.
- Avoid sending sensitive information over email or texts.
- Back up information so that you have another copy.
- Apply software updates and patches.
- Filter spam emails (unsolicited junk emails sent in bulk).
- Block IP addresses, domain names, and file types that you know to be bad
Call the sender to verify legitimacy (e.g. if you receive a call from your bank, hang up and call them). - Use anti-phishing software that aligns with the Domain-based Message Authentication, Reporting, and Conformance (DMARC) policy
Reduce the amount of personal information you post online (e.g. phone numbers and extensions for employees). - Establish protocols and procedures for your employees to internally verify suspicious communications. This should include an easy way for staff to report phishing attacks.
- Use multi-factor authentication on all systems, especially on shared corporate media accounts.



