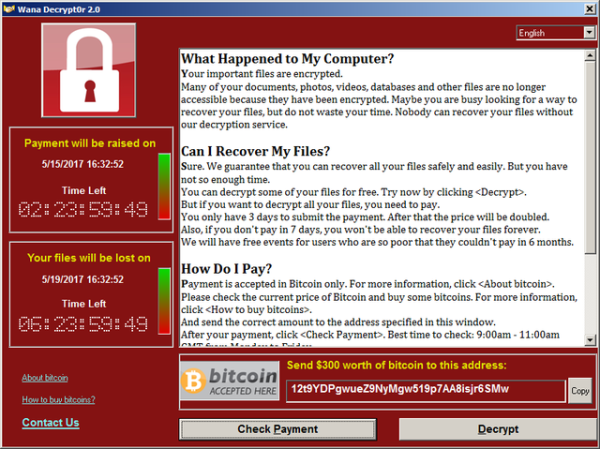
Malware found in more than 190 Android apps
SpinOk malware has been found in multiple Android apps that have been downloaded more than 30 million times. The malware-riddled apps were found on the Google Play store, following an investigation by cyber security company CloudSEK. Following their investigation, the research team found that 193 apps on the Google Play store were infected with malware, 43 of which were active within the last week. SpinOk malware was first discovered by cyber security software company Dr Web in May 2023. Distributed as an advertisement software development kit (SDK), the Trojan malware actually acts as spyware. Dr Web found in May that…