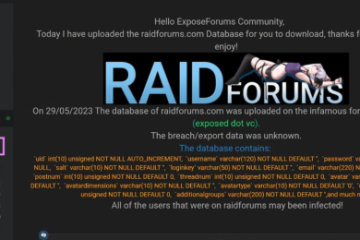
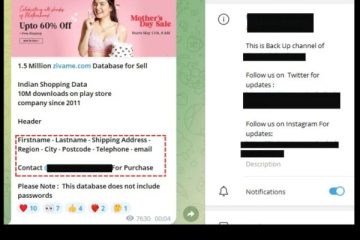
Only 1 Percent Of Attacks On Critical Network Infrastructure; Majority Of Attacks On People

We respect your privacy, by clicking “Download Your Copy” you agree to having your details passed onto the sponsor who may promote similar products and services related to your area of interest subject to their privacy policy. You have the right to object. In addition, you will receive our e-newsletter, including information on related online learning opportunities. For further information on how we process and monitor your personal data, and information about your privacy and opt-out rights, click here. Download Your Copy
Cyber criminals continue to refine techniques that target people rather than infrastructure, with attacks that rely more on human interaction and less on automated exploits.
Regardless of the means of attack—email, cloud applications, the web, social media, or other vectors—threat actors repeatedly demonstrated the effectiveness of the social engineering tactics that convinced victims to click malicious links, download unsafe files, install malware, transfer funds and disclose sensitive information at scale. Whether financially motivated or state-sponsored, attackers all had one thing in common: an understanding of and a willingness to take advantage of the human factor.
Based on the analysis of data collected from more than 1 billion messages per day, this report explores the role of human factors on enterprise cyber security strategy.
Important enterprise security questions addressed in this report include:
- The Top 20 phishing lures
- Ten industries most-often targeted by malware campaigns
- People-centered attack metrics that you can benchmark against your organization
We respect your privacy, by clicking “Download Your Copy” you agree to having your details passed onto the sponsor who may promote similar products and services related to your area of interest subject to their privacy policy. You have the right to object. In addition, you will receive our e-newsletter, including information on related online learning opportunities. For further information on how we process and monitor your personal data, and information about your privacy and opt-out rights, click here. Download Your Copy