Russia-linked ransomware gang ALPHV has claimed to have launched a cyber attack against Amazon-owned domestic security company, Ring.
Ring, which makes doorbells with video and sound recording capabilities, has denied that the hack took place. ALPHV, however, posted on the dark web about the hack and is threatening to release data stolen during the breach.
The gang, which is responsible for creating BlackCat malware, posted a picture of the Ring logo on its website alongside the phrase “There’s always an option to let us leak your data”.
Ring LLC, the home security and smart home company owned by Amazon, has been ransomed by ALPHV ransomware group.
They left a simple message to Ring: “There’s always the option to let us leak your data”. pic.twitter.com/RfrvpXBgGh
— vx-underground (@vxunderground) March 13, 2023
In a statement to Techcrunch, Ring spokesperson Emma Daniels said there were “no indications” that Ring had been the victim of a “ransomware event”.
Ring also said in a statement to Vice that while the company was aware of a third-party vendor that was the victim of a ransomware attack, that company does not have access to Ring customer records. Ring said it would be working further with the company in question to find out more about the cyber attack.
Vice alleged in the same article that an earlier version of its coverage was shared on an internal Amazon Slack channel with the message: “Do not discuss anything about this. The right security teams are engaged”.
ALPHV is notorious for targeting companies, organizations and educational institutions with its ransomware in an attempt to extort them.
BlackCat ransomware attack against the University of Pisa
In June 2022, the University of Pisa was targeted by ALPHV’s BlackCat ransomware.
It was discovered that the ransomware gang planned to target the university on June 11, 2022, as ALPHV posted a message to its website that read: “Let’s play, the university goes to sleep, the mafia wakes up?”
A BlackCat ransomware attack was launched against the university shortly afterwards. Italian news site Cybersecurity360 reported that the gang requested a US$4.5mn ransom by June 16, 2022, noting that the amount would increase to $5mn if the date passed without the gang being paid.
The outlet shared a screenshot of the compromised network page which appears to invite the victim to speak to the gang about the ransom via an online chatroom.
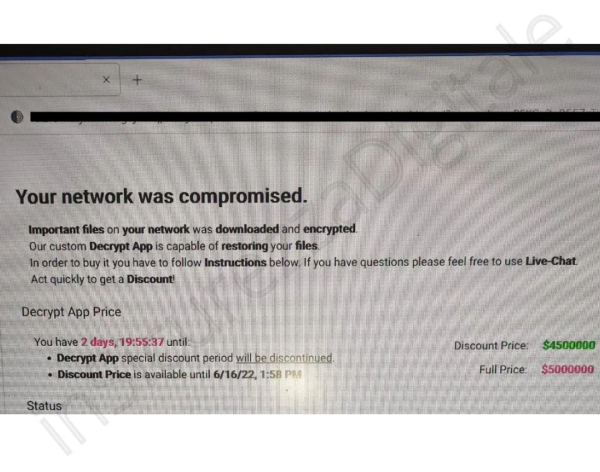
Image source: Cybersecurity360
The university did not publish any details concerning whether it paid the ransom on the date required.



