This article explains what carding is, how hackers can gain access to payment details and the effects carding cyber attacks can have on businesses.
In the first six months of 2022, there were 230,937 credit card fraud reports filed in the US alone, highlighting the growth of carding as a threat vector
This article will explore carding, how it operates and the devastating effects it can have on ecommerce businesses.
Contents:
- What is carding and why you should be aware of it?
- How do attackers acquire details for carding?
- The BidenCash carding incident
What is carding and why you should be aware of it?
Carding refers to the trading and unauthorized use of stolen credit card details over the internet. Card details can be seized by hackers during data breaches and used to commit financial fraud. To cover their tracks, hackers can use the stolen details to buy prepaid gift cards.
Carding marketplaces are dark web sites that deal in the trade of stolen credit card numbers, allowing those who download the details to commit financial fraud using card stuffing techniques.
Credit card stuffing is a technique used by hackers to repeatedly try to authorize stolen credit card details. Carding is often performed by automated systems as it allows them to rapidly input numbers.
How do attackers acquire details for carding?
There are numerous threat vectors malicious actors can employ to seize credit details. Below are examples of the prominent techniques used in this cyber crime.
Phishing
Phishing is a social engineering tactic where hackers attempt to gain access to personal or confidential information by posing as a legitimate company to the victim.
Malicious actors can use a variety of channels to send phishing links including texts, social media messages and emails. In fact, I recently received an email from hackers attempting to phish me by posing as Apple.
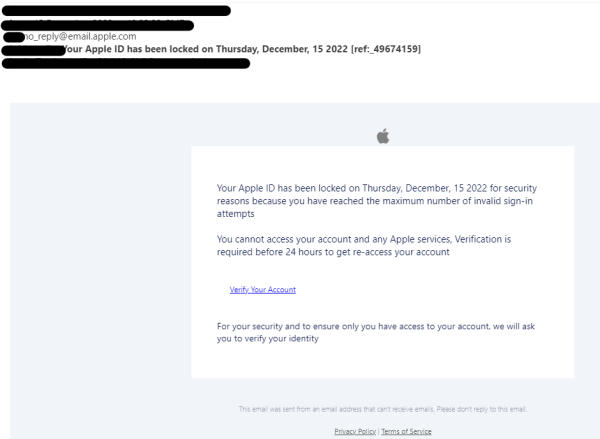
This email is intended to incite strong emotions in the recipient and get them to click on the link and enter whatever information it asks for without thinking. The use of a spoofed ‘no reply’ email address and a reference number also serve to make it look more legitimate.
In this case, hackers were looking to gain access to my Apple ID credentials, including my email and password. If they pose as an ecommerce site, or any other entity that would require me to enter my payment card information, they could steal it this way.
Hackers can also gain access to credit card information by sending phishing links to companies who store customer payment details to collect employee login information. This information can then be used to access internal data storage systems to steal full or partial card details.
Web skimming
Web skimming involves malicious parties inserting malicious code into sites that process payment card information such as ecommerce sites. The malicious code extracts data customers input into HTML forms (namely payment card details) into the site and relays it to the hacker.
A piece of software known as Magecart has been used by hacking groups to steal payment details from ecommerce sites, with prominent victims being American online retailer Newegg and the merchandise site for conspiracy site InfoWars.
BIN attacks
Bank Identifying Number (BIN) attacks which see fraudsters take incomplete card details gained during phishing or social engineering attacks (i.e., the first six numbers of a bank card) and use automated software to randomly generate the rest of the information needed.
The malicious actors will then use ecommerce sites to test whether the details are correct or if the cards are active. If it is confirmed that they are, they can then either sell the details on or use them to buy gift cards.
How can carding affect businesses?
As with any cyber attack, carding can have a lasting impact on businesses. Research by the Ponemon Institute has found that 65 percent of businesses report that data breaches negatively affected customer perception of them, leading to lost custom and a decrease in profits.
The institute also found that the average cost of a data breach on a business is US$4.24m, with $1.61m (38 percent) of this coming from lost business after the breach. If a business suffers a carding attack and customers’ details are stolen, they may feel as though the company has either mishandled or not adequately protected their data. This may lead to them filing a class action lawsuit against the company.
Additionally, if customers do become victims of further cyber crime like financial fraud as a result of a carding-based cyber attack, this will further negatively affect their view of the brand potentially leading to more loss. This is why over seven in ten (71 percent) of CMOs believe the biggest impact of a data breach is the loss of brand value.
The BidenCash carding incident
⚠️ #BidenCash after 4 months shared a new credit card dump of over 1 million users!
ℹ️ These cards mainly come from web skimmers!
🚨 The archive contains: PAN, CVV2, Expiration date, Name, Surname, Shipping Address and Email!
We are analyzing the data, more details soon! pic.twitter.com/bR1NuNdeSF
— D3Lab (@D3LabIT) October 7, 2022
In October 2022, BidenCash, a dark web carding marketplace, released the full details of more than 1.2 million stolen credit cards for free.
A file containing the information for 1,221,551 credit cards, mostly originating from within the US, expiring between 2023 and 2026. The post also included other details needed to make online transactions including victim’s names, bank names, social security numbers, email addresses, phone numbers and addresses. The information was also shared on other hacking and carding forums.
BidenCash has been operating since June 2022, when it leaked the details of several thousand cards to promote the site.
The new, larger release of credit card information may also be a way to promote the site’s domain, as BidenCash was forced to launch new URLs in September after it suffered a series of denial of service (DDoS) attacks.
The credit card information may have been stolen using a number of threat vectors, including malware or hacking ecommerce sites. Additionally, some details in the release may be recycled from older releases, including the All World Cards release which saw the details of more than one million stolen credit cards posted on hacking forums in August 2021.



