The US Marshals Service (USMS), a federal law enforcement agency within the US Department of Justice (DoJ) has announced that it was the victim of a ransomware attack that compromised confidential information held by the agency.
The attack, which took place on February 17, saw “a ransomware and data exfiltration” attack launched against a “stand-alone USMS system”.
The system compromised in the attack held a number of sensitive documents, including “returns from legal process, administrative information, and personally identifiable information pertaining to subjects of USMS investigations, third parties, and certain USMS employees”.
Chief of the USMS public affairs office, Drew Wade, told Reuters that the service had reported the data breach to the US Department of Justice, who then began a forensic investigation into the attack.
The DoJ has branded the cyber attack a “major incident”, which, according to the United States Computer Emergency Readiness Team (US-CERT), is an incident which is “likely to result in demonstrable harm to the national security interests, foreign relations, or economy of the United States or to the public confidence, civil liberties or public health and safety of the American people”.
Major incidents caused by ransomware
US-CERT also notes that cyber attacks classed as major incidents “demand unity of effort within the Federal Government and especially close coordination between the public and private sectors as appropriate”.
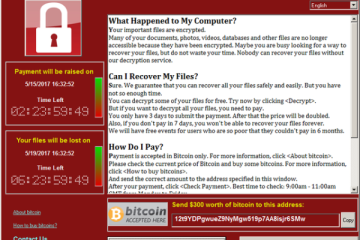
This is the second time in two months that a large-scale government office has been directly targeted by a ransomware attack, with the United Kingdom’s Royal Mail service suffering an attack in January.
On January 11, a cyber attack against the UK postal service Royal Mail led to a request that customers stop sending mail abroad via its services. The attack was later linked to Russian hackers.
Royal Mail said the cyber attack caused “severe disruption” to the computerized systems used to send mail abroad. The company “immediately launched an investigation into the [cyber] incident” and utilized the help of the UK’s National Cyber Security Centre, Information Commissioner’s Office and National Crime Agency to halt further attacks.
Hackers targeting postal services
The system affected by the cyber attack was used at six Royal Mail sites to track and trace items sent abroad, as well as to prepare mail to be dispatched overseas.
On January 12, it was reported by multiple news sites that the incident was in fact a cyber attack against Royal Mail by Russian ransomware-as-a-service (RaaS) gang LockBit.
Printers at a Royal Mail distribution center in Belfast, Northern Ireland, began to print letters from the gang. The letters allegedly informed those in the office that LockBit black ransomware was responsible for the disruption and that “your data are [sic] stolen and encrypted.” A threat was issued to post it online if the ransom demands were not met.
[Embed tweet: https://twitter.com/rowlsmanthorpe/status/1613607240316878873 ]
Royal Mail did not publicly say that LockBit was responsible for the attack.